Password Security
i don't want to change my password
Chuck's Cyber Wall
As a cybersecurity expert constantly preaching Password Security, I don’t know how often I’ve heard the phrase – I don’t want to change my password.

Let’s be clear; this is not something I tell people because I want to make their lives difficult or to test their memory, or because I like to see them suffer. In fact, I love the NIST guidelines on passwords which are far more user-friendly. These new guidelines include reducing complexity, removing periodic change requirements, and allowing spaces to use easy-to-remember phrases. This is way better than the ridiculous rule – at least one number, at least one letter, a capital letter, and a symbol – that we all hate.
Not only were the previous password guidelines based on a white paper written in the mid-1980s, but the man who wrote the guidelines, Bill Burr, admits he wrote it without knowing how passwords work. That’s right, all of this suffering with complexity rules and constantly changing passwords was based on bad information. So now, after nearly two decades of painfully dealing with these password requirements, the security rules are evolving.
Unfortunately, evolution is a slow process, and it will be a while before these new guidelines are adopted, as there are other security components to consider, such as multifactor identification. But for me, the best part of this rule is that passwords only need to be changed if there is evidence of a potential breach.
So let’s talk about a potential breach.
Potential Breach
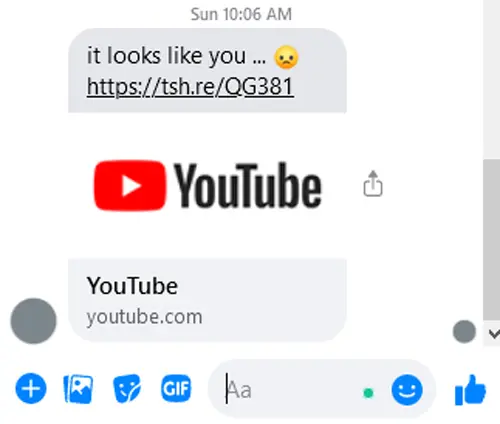
This weekend, a relative had their Facebook account hijacked, sending a YouTube video link to those on his friend list. Like most people, I wanted to see what internet fun he chose to send me, but…
- he never sent me a video link before
- the link didn’t generate a video preview
- a YouTube logo was included but wasn’t in the link
That was enough for me to hit the brakes. Instead of clicking on the link, I went to Norton Safe Web and typed in the web address.
DO NOT copy and paste suspicious links – it’s too easy to accidentally paste them into a browser.
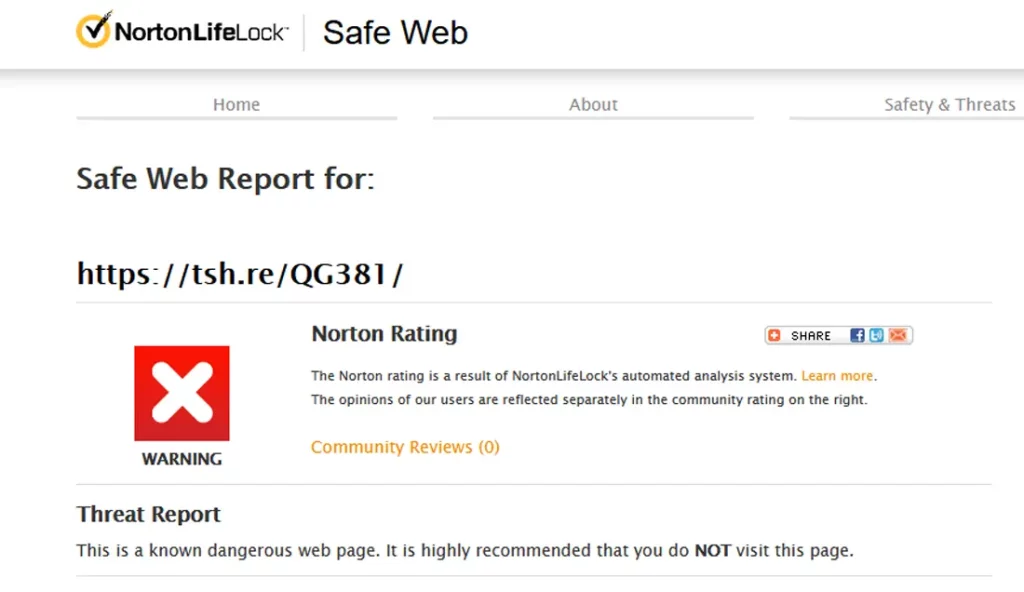
Seeing it marked as malicious, I decided to dig a little further and used an old laptop connected to a segregated network to see what would happen when I clicked on the link.
I discovered that clicking the link takes you to a page that prompts you to enter your Facebook username and password on a fake login page. Except it sends your user information to cybercriminals, who will then use it to send malicious links to your friends and family.
But we’re not done yet. The page also includes malicious code that runs in your computer’s memory, scanning for passwords. So even if you don’t fall for the credential theft or close the browser, it keeps running.
This code saves the data in a temporary file and then sends it to a remote server operated by cybercriminals.
This is what we call a potential breach. And what did we say above about a potential breach – passwords need to be changed.
The Problem With Reusing Passwords
I posted a message advising anyone who clicked that link to change their password. While I have no way of knowing how many took my advice, I did get responses from people who clicked on the link and said nothing happened, so they saw no need to change their password. Now let’s take this response and amplify it a little because not only is it necessary to change the Facebook password, but any account that uses that password also needs to be changed.
Why?
Because while most companies go to great pains to protect passwords, user names are much easier for hackers to get. On top of this, most people use our first or last names as part of the user name for official accounts, such as finances and business. That practice has trickled down into social media and entertainment accounts. This means that if cybercriminals get your social media password, they have bots that will then run that password against other user accounts that belong to you. This process is called credential stuffing.
That makes sense, right? Yet, many people simply refuse to go through the effort to secure their accounts. This is why cybercriminals still use these tactics and continue to be so successful.
Ha My Username Or Password Been Breached?
Believe it or not, you don’t need to be a cybersecurity expert to determine if your username or password has been involved in a breach. There are two simple websites available to anyone that tracks information involved in breaches that have shown up on the dark web. Of course, not every breach gets put up for sale on the dark web, but if you’re wondering about a particular email address or password, these are great tools.
The website to check your email address is Have I Been Pwned?, and the one to check your password is Pwned Passwords.
There have been so many data breaches that anyone who spends time online should be taking an active role in keeping their digital identity safe. It all starts with finding out if your information has been involved in a breach and then taking steps to resolve it. In other words, change your password!
Final Thought
Cyber criminals don’t target people, they target vulnerabilities with automated attacks. So the only way to keep yourself safe is to be cyber aware! We’re cybersecurity experts, if you want help installing a good antivirus, choosing a password manager, or just figuring out where to start, we can help. Contact us at 301-456-6931 or send an email to [email protected] for a free quote.

Director of Cybersecurity and Marketing
I’ve always had a love of working with technology, being fortunate enough to have grown up with a grandfather who taught me how to fix things for myself and not be afraid to jump in and get my hands dirty. Over the last three decades, I’ve worked as a technician, trainer, technical writer, and manager in small businesses, enterprise organizations, and government. In addition, I’m an author, having published multiple works available online and in print. You can find my creative work at https://WritingDistracted.com

