don't get phished
Chuck's Cyber Wall
At CLARK, we get a lot of questions from our customers about the various cyber threats out there. The one cyberattack that we’ve all seen is the Phishing scam. Still, most people don’t really understand what it is or what they can do about it, so I’m going to break it down for you.
WHY DO THEY CALL IT PHISHING

Why do they call it Phishing?
There’s a perfectly good reason for it. Even if you’ve never gone fishing, you know how it works:
- Get out your fishing pole
- Put the bait on the hook
- Cast it into the water
- Wait to catch a fish
Out in the cyber world, it’s basically the same thing:
- Buy email addresses from the dark web
- Craft an email with fake links
- Send the email to as many people as possible
- Wait to see who clicks on it
Phishing is a Numbers Game!
The scammers who make these attacks hope you’re not paying attention. They count on you to trust something that looks familiar or react before you can think about it. In short, they prey on the busy, the unaware, and the lazy. Any one of the three are potential victims that can be exploited—and that covers an ocean of people.
What are these scammers trying to catch?
Quite simply, they want your information.
- Email addresses
- User Names
- Passwords
- Contact Lists
No matter how important or unimportant you think you are, all of your information has value. It is just as true in marketing as it is with cyber criminals, all digital information can be used to make money.

Scammers buy email addresses and contact lists to build new phishing attacks. They utilize or sell user names and passwords to breach networks, steal money, and gather personal information for everything from identity theft to personalized marketing scams to network intrusions.
Every bit of information they can get has a dollar value on the dark web.
How do you outsmart the hackers?
How Do You Outsmart the Hackers?
The short answer, pay attention to every email. There are five simple ways to avoid being a victim.
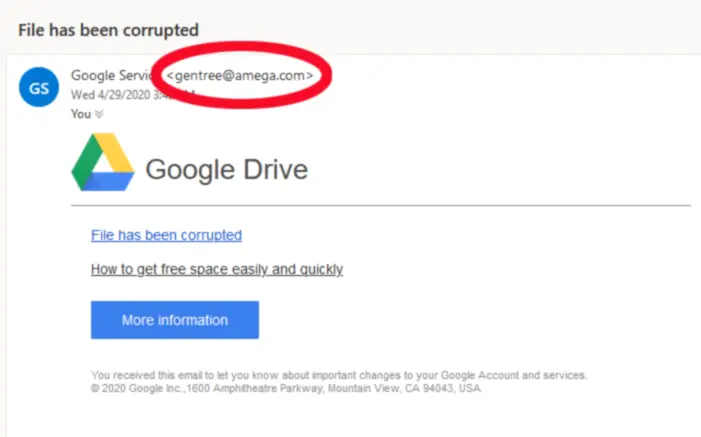
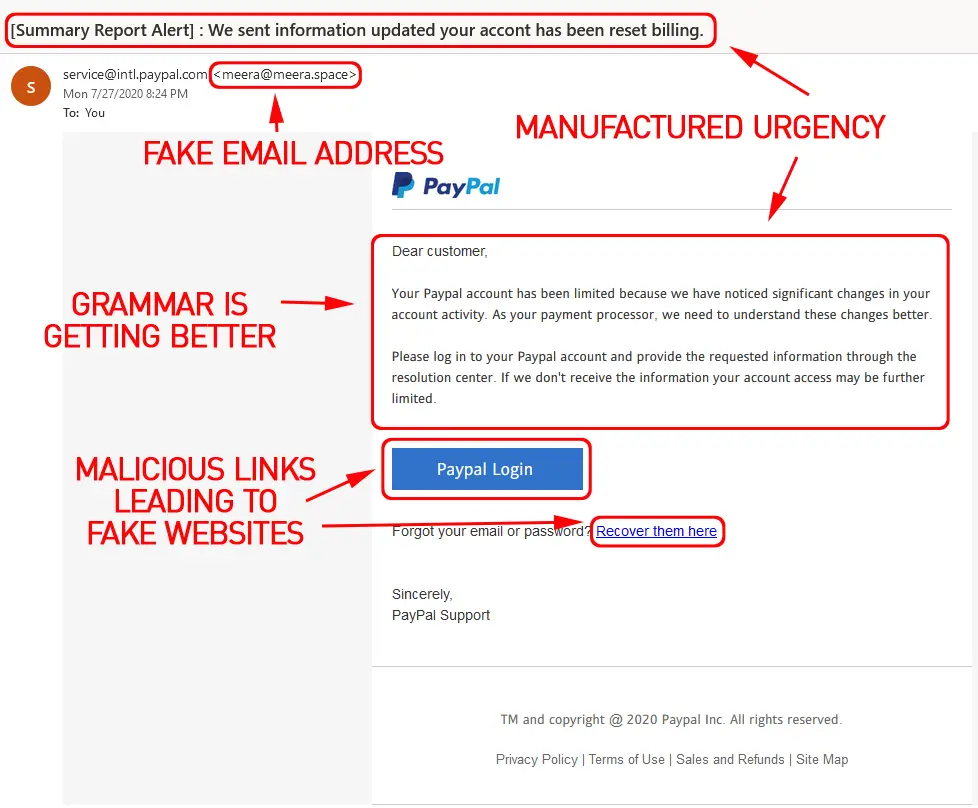
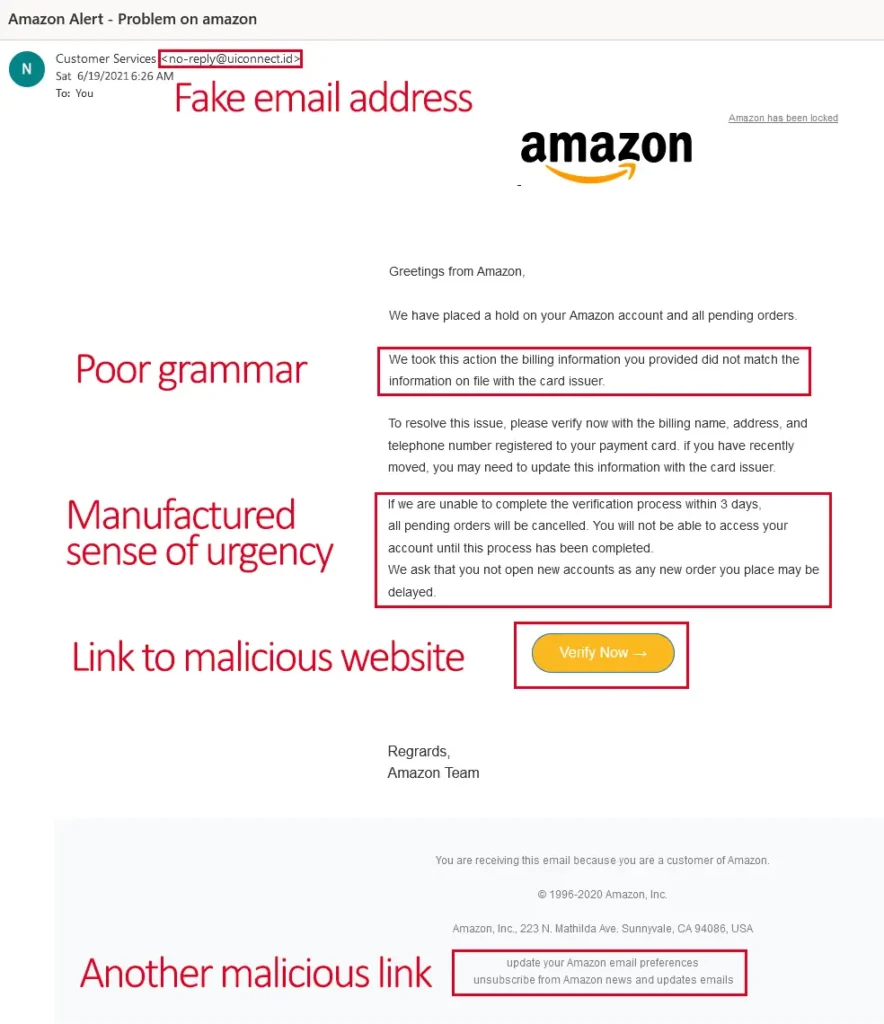
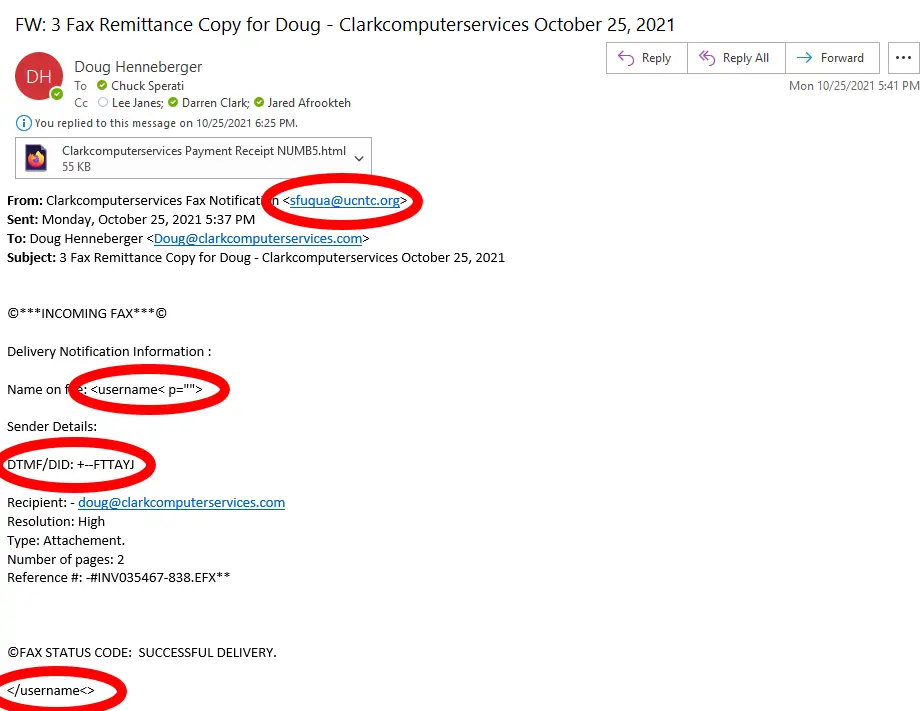
#1 Look at the Email Address, not just the Sender’s Name
No legitimate organization will ever contact you from a public domain, i.e., @gmail, @yahoo, etc. The problem is that most people don’t even look at the email address, only the display name and subject line. Phishing scammers are clever—in addition to creating a fake email address, they also create fake display names.
Because of this, people who receive them tend to jump directly to the content.
But scammers don’t depend on this alone. Good phishing emails also include the correct banners and color schemes to mimic the organizations the email is crafted around. All of it is a distraction to keep you from looking too closely at the email address because those fake email addresses are an obvious giveaway of the scam. Phishing emails evoking Apple, Netflix, Paypal, and Amazon are widespread because their logos are common and many people have accounts with them, so if you’re not paying attention, they’ve got you on their hook!
#2 Pay attention to Spelling
As I said before, scammers are clever. They use minor misspellings to fool you into thinking an email address is legitimate. It’s easy to mistake rnedia for media if you aren’t paying attention.
Scammers are the ultimate A/B testers, learning from successes and failures. They know that the email address is the biggest giveaway of the scam, so they try to compensate for it by making the domain name spelling close. Since anyone can buy a domain name from a registrar so long as that name is not currently used, they use simple misspellings such as Anazon, Neftlix, and Appel to fool you.
The goal is to make the email seem legitimate at first glance. I’m going to repeat this because it cannot be said enough, the bets way to foil these hackers is to pay attention. Go back and re-read that last line again.
Did you see what was written or what you expected to see?
#3 Read the Content of the Message
While odd phrases and blatant grammatical errors are indicators of fake emails, scammers use spell checkers, so spelling mistakes are rare, but if you see a string of missed words, it’s probably fake.
Wait-a-second. I keep telling you how clever these scammers are, but why would there be blatant grammatical errors if they’re so smart? The short answer is that many of them either aren’t very good at writing or are from non-English speaking countries. On the plus side, that makes it much easier to pick up the differences between a simple typo made by a legitimate sender and an error indicative of a scam.
Using spell-checkers and translators might give them the right words, but it doesn’t always provide the right context. Look for missing words, grammatical incoherence, and language consistent with previous messages you’ve received from the person or organization. If you’re in doubt, don’t respond to the email. Use an alternate method of communicating with them, i.e., use an alternate email, go to their website, call, etc.
#4 Suspicious Attachments and Links
No legitimate organization will ever send you an unsolicited log-in link or ask for your username or password. Only hackers and scammers do that. If you receive an invoice, receipt, or link from someone you don’t know or an email address that looks wrong, don’t click on it!
Attachments and links are the malicious payloads that cybercriminals deliver. Let’s take a closer look at these.
Attachments typically come as documents or PDFs, disguised as receipts or invoices, but they can be compressed folders, voicemail messages, pictures, or videos, among others. It doesn’t matter if the recipient is expecting the attachment. All that matters is that they open it. Once open, the malware is unleashed on the computer, and you are on their hook!
The best advice I can offer is never to open an attachment unless you are confident it’s legitimate, i.e., it’s something you expect and relevant to your duties. Even then, it’s prudent to look for anything suspicious in the content—don’t ignore other indicators just because you often receive attachments.
Links are a little more tricky as they can be a button, embedded into a phrase, attached to a picture, etc. Scammers do this because the destination link won’t match the context of the email, making it another dead giveaway of a scam. Malicious links often point to fake websites with log-in boxes designed to steal credentials.
How can you know if the malicious link is hidden in a button or image?
It’s actually pretty easy. On a computer, you can hover your mouse over the button, and the full link will appear in a small bar at the bottom of the browser. Hold your finger on the link on a mobile device, and you will get a popup with the full link. To avoid getting hooked, train yourself to always check the links before opening them.
#5 The Message contains a Sense of Urgency
Scammers don’t want you to think about the email scams because the longer you think about them, the more likely you will realize it’s a scam. For this reason, they manufacture importance, using threats, short reward periods, and risks of missed opportunities to get you to act now!
Think before you click.
Scammers understand that the more time we have to think about things, the more likely we will pick up on clues. Therefore, they prey upon our fears of missing out or acting before it’s too late. A manufactured sense of urgency is especially effective in workplace scams, as the scammers know that most people will drop everything else when the boss has an important request.
The more urgent the email appears, the more caution we should exercise before responding.
Everyone has heard of the assistants who went out and bought $1500 of gift cards based on a scam email. Of all the tools that scammers use, none are quite as effective as a manufactured sense of urgency because it focuses on the call to action and off the clues.
With every success and failure, hackers are learning. Phishing attacks are getting more advanced, using better lures, and casting more than 3 billion scam emails each day. Don’t end up dangling on the hook.
Look for clues.
Think before you click.
Outsmart the hackers and just keep swimming.

Director of Cybersecurity and Marketing
I’ve always had a love of working with technology, being fortunate enough to have grown up with a grandfather who taught me how to fix things for myself and not be afraid to jump in and get my hands dirty. Over the last three decades, I’ve worked as a technician, trainer, technical writer, and manager in small businesses, enterprise organizations, and government. In addition, I’m an author, having published multiple works available online and in print. You can find my creative work at https://WritingDistracted.com