How to maintain
cyber awareness on social media
Chuck's Cyber Wall

Security awareness is vital on the internet, especially on social media.
Facebook. Twitter. Instagram. Tik-tok. LinkedIn. Pinterest. Whatever your flavor, there’s a ton of content out there vying for your attention. For most of us, it combines communication and entertainment into a safe social distraction, but for cybercriminals, it’s a gold mine of information waiting to be exploited. Where social media allows us to watch cat videos, share pictures and memes, make comments, and play games with friends and family, they aren’t the only ones watching.
Cybercriminals are laying traps to steal your information, baiting them with fake friend requests, games, and false news snippets.
But with a bit of awareness, you can avoid the bait, and we’re going to start with the most successful way for hackers to steal your password and identity.
Quizzes
I’m sure you see them every day.
- How well do you know me?
- Fun facts you might not know about me.
- Personality tests.
- What TV/Movie character are you?
What’s more mind-boggling than the proliferation of these online quizzes is the number of people who take and share them. Security experts estimate that more than 75% of these tests are designed by hackers with the sole purpose of asking seemingly silly or meaningless questions that can then be used to successfully guess passwords and answer security questions. In fact, many of the questions included in these quizzes are taken directly from the security questions used by the government, financial institutions, and retail websites.
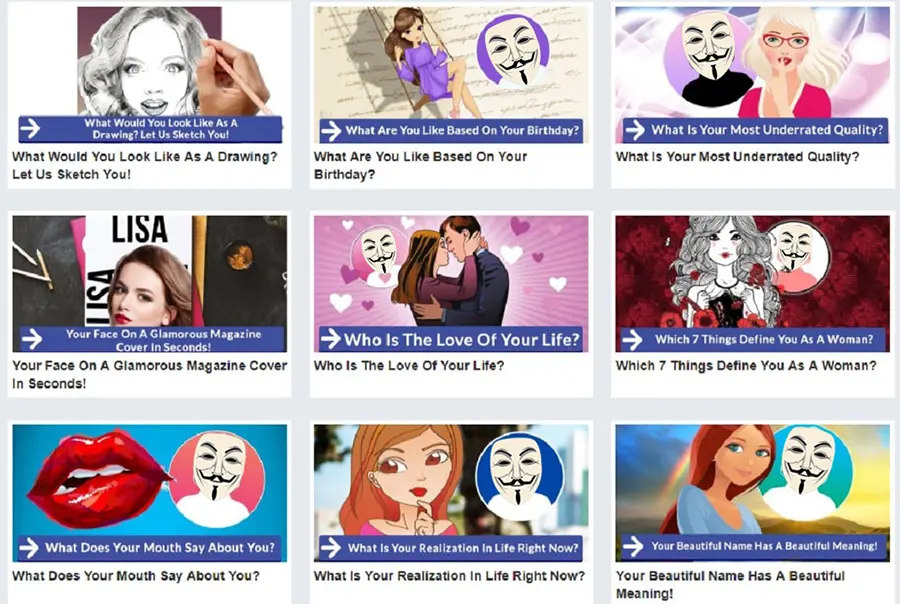
On the dark web, every piece of personal information has a dollar value, and every time someone takes one of these online quizzes, there’s a good chance they’re sending their information to hackers. These are not targeted attacks. Bots disperse them, and they collect information indiscriminately. These types of attacks are why cybersecurity experts are constantly explaining that everyone is a target. And yet, social media continually proves that all the hackers have to do is package personal questions in a fun and entertaining way, and people are more than willing to hand over their information.
While not all social media quizzes are used for data collection, enough of them are that it’s better to be skeptical and avoid them altogether. And if you’ve taken any of these quizzes, it’s best to delete them from your timeline.
Fake Friend Requests
A favorite ongoing activity for hackers is stealing images to create fake profiles.
Stealing images from a social media platform is a lot easier than you might think. Screen captures are effortless on computers and mobile devices. Anyone can create a social media account with a valid email address. And with so many people having similar names, creating a passable email address is not exactly challenging. Add a stolen picture, and you have a fake profile.

From there, it’s just a matter of sending invites to friends and coworkers.
Let’s face it: we love to talk about our lives – whether it’s family, work, or this morning’s traffic. We reveal all kinds of things about ourselves that cybercriminals can use. If you’ve adjusted your privacy and security settings to make sure that your ramblings are available only to friends, then you’re safe, right?
Not really. These settings will make you more secure unless you accept an invite from a fake friend. Accepting that fake friend request opens your entire timeline or feed – and your friends – to cybercriminals. This is why cybercriminals go to the trouble of creating fake profiles and sending out friend requests.
With that in mind, before you accept a friend request:
- Check to make sure you’re not already friends
- From within the social media platform, search for the person who sent the friend request and check for duplicate profiles
- Look at the profile – is there anything in their timeline? Do they have any pictures posted? Is the About section blank?
- If something looks phishy, ignore the friend request, report it, or reach out to the person in a different way
Fake friend requests rely on people not paying attention and blindly accepting invites. Be aware and watch out for yourself and your online friends.
Share Wisely
We all know that social media is full of fake news, no matter what side of whatever fence you stand behind. Add to that the extremists, conspirators, and hackers, and now we have false, misleading, or nefarious links posted all over the place.
Many assume that if a friend is sharing it, then it must be trustworthy.
This assumption could not be further from the truth. Anything shared on the internet should be viewed with a degree of skepticism.
People typically share because it resonates with them on some level, positively or negatively. Hackers have made a living by posting blatantly false information embedded with malicious links with the only goal of getting people to comment, click, and share. Social media platforms are doing more now than ever before to limit this, but it takes time to catch everything, and that little bit of time is all cybercriminals need to wreak havoc on someone’s life.

Before sharing anything:
- Hover over the link to see where it really leads, and if it looks phishy, leave it alone or report it
- If anything prompts you to download or install an app or file, cancel immediately and stay away
- Watch out for brand impersonators – it might have a recognizable logo, but that doesn’t mean it’s legit
- Pay attention to who you follow – if they share suspicious links, they might expose you to social media scams
- Above all, be careful about what you click on, and don’t believe everything you read
When it comes to security, awareness is key – in email, on social media, walking down the road. Keep your eyes open, remain alert, and stay safe.
If you’re not sure where to get started with cybersecurity, give us a call at 301-456-6931 or send an email to [email protected] and see why we are simply the Best Choice in IT Support Services.

Director of Cybersecurity and Marketing
I’ve always had a love of working with technology, being fortunate enough to have grown up with a grandfather who taught me how to fix things for myself and not be afraid to jump in and get my hands dirty. Over the last three decades, I’ve worked as a technician, trainer, technical writer, and manager in small businesses, enterprise organizations, and government. In addition, I’m an author, having published multiple works available online and in print. You can find my creative work at https://WritingDistracted.com

